Body Talk.. Kick off your dancing shoes
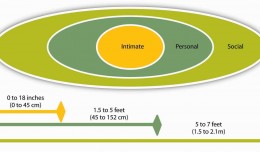
The human body is a wonderful thing, I admit some more wonderful than others, but I digress. We all give of subtle signals, cues and tells. These are subconsciously taken in, but consciously we are not always aware of what is h...