Thought I would share some info on a text scam I got a few weeks ago. I setup a fake email account, got a burner number to make relevant calls and generated fake name, address, card number etc to see how these guys would respond.
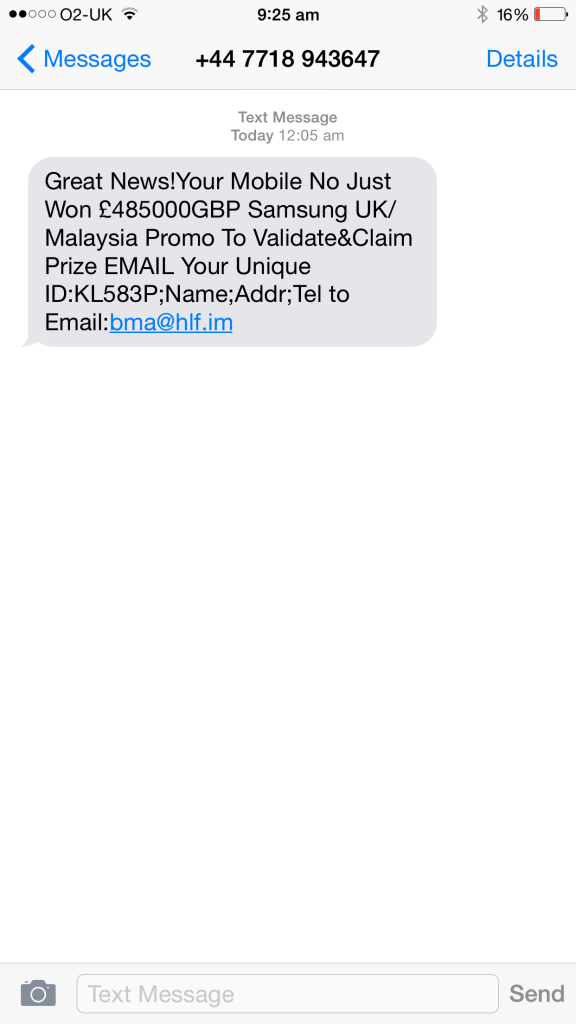
Below is the original text message, I never win anything so imagine my amazement to win this Samsung promo 🙂
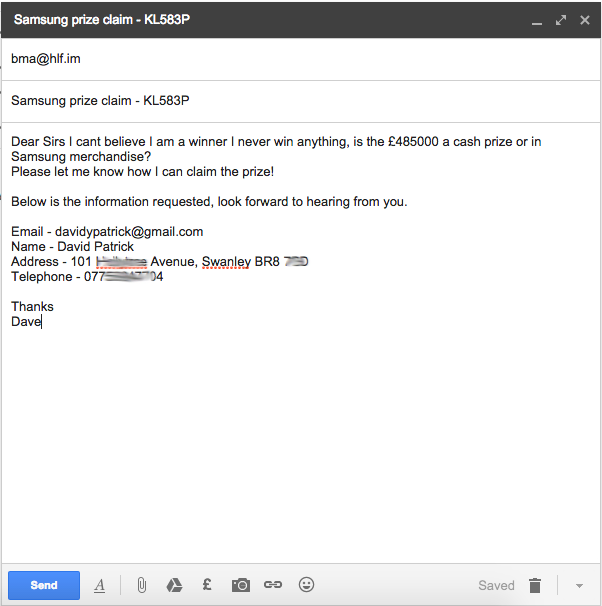
So with fake info created using various generators, and a new SIM card acquired I felt I must respond, I mean thats a nice win 🙂
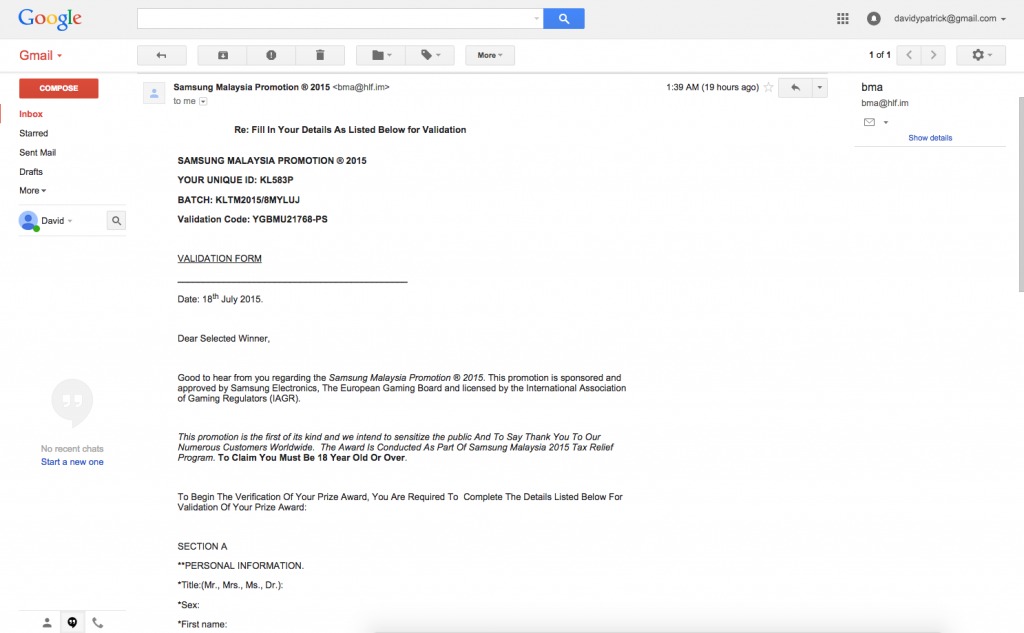
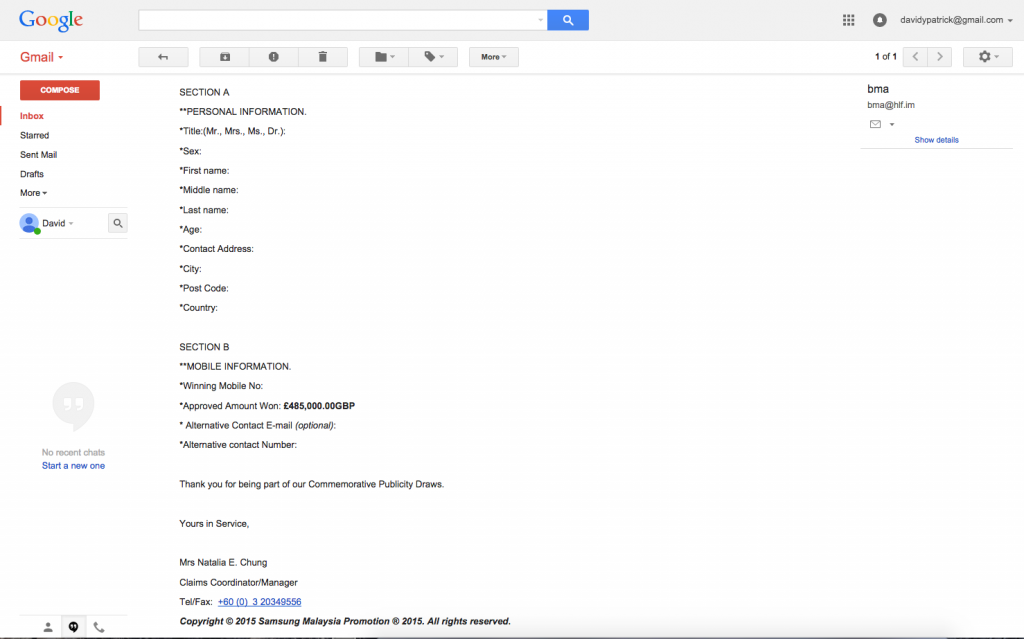
So I had provided them with all the info requested, so I just needed to wait for the cash to roll in. However surprisingly they asked for the same information again pretty much.
So … I provide all the needed info again and assume they will follow up asking for some form of payment, or credit card info to validate ID or something. But nothing 🙁 That was the end of it. So I can only assume they then look to utilise the data taken here for identity theft purposes. I have had other emails from the same number, so there isnt much intelligence going on in who they target, but if you get texts or emails similar to this, just delete them, share no info and respond to nothing.
Today as I wrote this, I got another one on a different number, this time I have some money waiting for a recent accident claim I never had, just one magic click to cash in 🙂
This isnt a particularly interesting post, more of a public service piece to share the numbers, email and site info so people get the scam results when searching, cheers for reading.










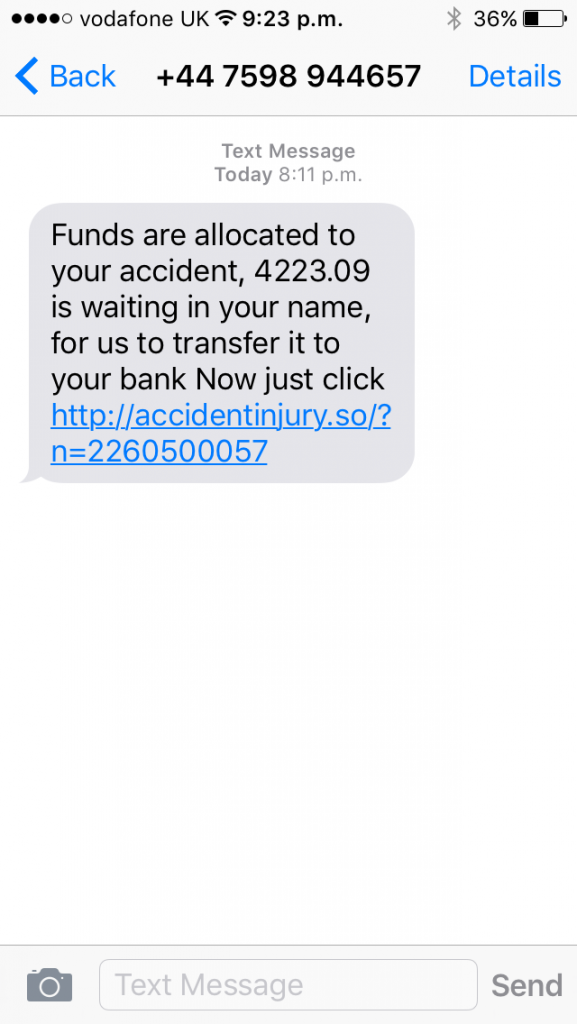







They usually use SIMBOXING, a box that uses multiple disposable sims to mask their origin; Keep the burner on and the numbers should continually change?