Proxemics is all about that little bubble we like to call personal space, depending on how people position themselves in that bubble effects how we feel. Below is a generalisation on acceptable distances based on interaction, but its important to be aware that we are all individuals so all of our bubbles are different, and also different countries and cultures (you will know this if you have ever been to Hungary) have totally different concepts on what is acceptable in the personal space intrusion stakes.
So why is proxemics of any interest to you as a social engineer? Well when it comes to gaining physical access, looking to influence and / or manipulate someone this is really important. This is very much linked to your body language and other non verbal cues, but where you position yourself has an impact on how you are perceived, the position or structure you are trying to portray as well as territorial aspects you may be trying to convey with your physical positioning.
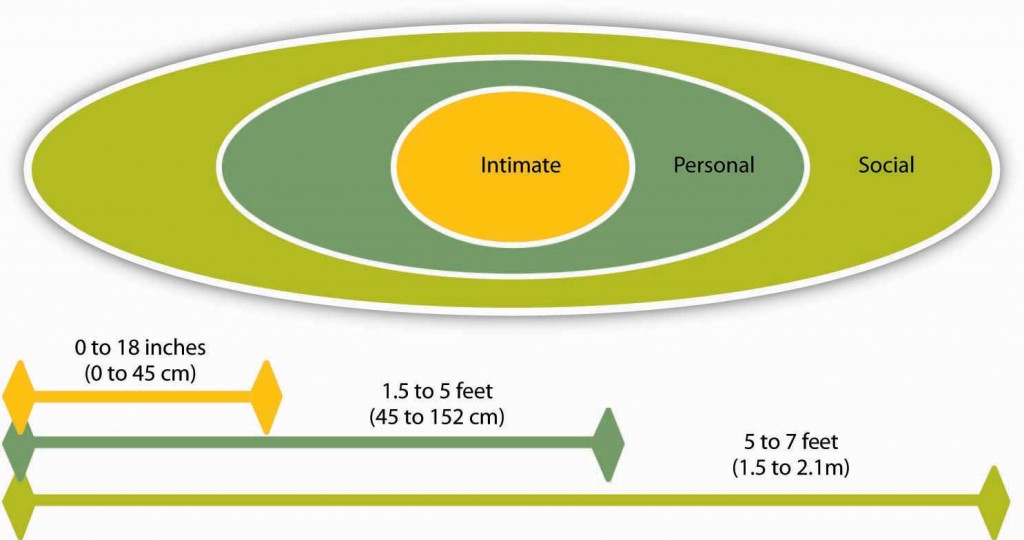
The social boundaries are what you would consider acceptable in a public / exhibition environment (not the local social club / pub). If you were waiting to meet someone, or speaking to a stranger to ask directions this is the typical personal space requirements that would be considered normal in most parts of the western world. Distances greater than the social boundary are more public spaces, like visiting a park, or museum, etc.
The personal boundary is the area I would imagine most people feel is invaded on a more regular basis. This area tends to be where we are happy for friends and close colleagues to venture into, and what we could consider a more ideal spacing if we are waiting for the bus. When people breach this boundary we can often feel threatened and looking to withdraw, or considering the option of standing our ground even though it may be an uncomfortable and stressful experience.
The intimate boundary is reserved for those we are most closest and trusting of, this is because at such a close range we are very vulnerable so trust is of paramount importance. A slight exception to this is when we are happy for us to whisper something we value to us, and for this we have happy to grant a temporary reprieve and allow that person in to share information, before getting the hell out.
As mentioned before, ethnicity and culture we will result in variances in this, but I quick bit of people watching will help establish a quick baseline of the cultural norm. You will of course experience the odd one out, who for variance reasons will keep a distance from you, or be all up in your face as part of their natural way of communicating, so even though it will feel awkward judge other non verbal cues to establish any possible intent before reacting. During our interactions people can possibly move through various boundaries depending on the social situation, intent of the interaction, the topic of discussion and even their gender.
So when you are next involved in an onsite engagement, and you are attempting to build rapport and influence individuals or groups be sure to give some thought to your proximity along with other verbal and non verbal cues we have discussed before.
Thanks for reading, and until next time happy hacking.

















Hi Dale, can I repost your article with a reference?
Sure.