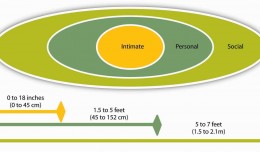
Looking forward to speaking at the 2018 ATM & Cyber Security Conference in October
I am excited to be confirmed as a speaker at the upcoming 2018 ATM and Cyber Security Conference in London this October. I will be speaking about building a Threat Centric Culture through Red Teaming, and how this can help prio...