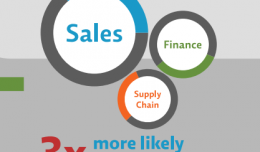
Hiding in plain sight… Playing it loud and proud
Happy New Year. 2011 has already gotten off to a hectic start for me, as I type this I am still in California working, but looking forward to flying back at the end of the week. In the last week I have tried out something a lit...