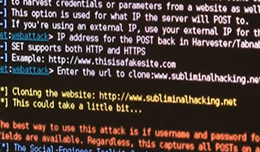
OSINT Tools … Recommendations List
Free OSINT Tools. With the New Year fast approaching I thought now would be a great time to post the first draft of some recommended Open Source Intelligence (OSINT) gathering tools and resources. I will look to maintain this l...