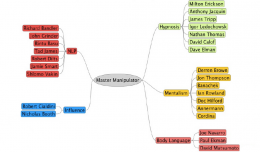
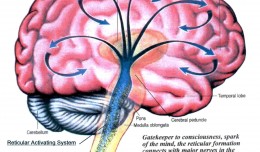
Pack up your troubles.. in your social engineering kit bag
Just a simple post this week, but you know what they say the best things come in the simplest of packages. 🙂 Like any good boy scout, you should always be prepared. So lets have a quick look at what we should have in our poc...